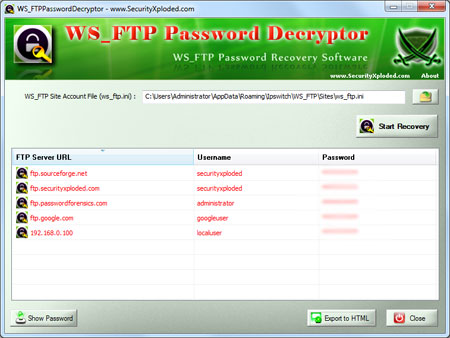
[NTFS Permissions Reporter] Display Windows User Access Rights
If you are working as a standalone user on a system running one of the latest flavors of the Microsoft Windows operating system, you do not really have much need to assess and verify user permissions on the system. If a PC is shared by many, and maybe even multiple users with administration rights, things may change significantly, as access rights become more difficulty to assess.
The free edition of
NTFS Permissions Reporter scans one or multiple of the computer’s hard drives for user permissions, and displays its findings in a report in the end.
NTFS Permissions Reporter Review
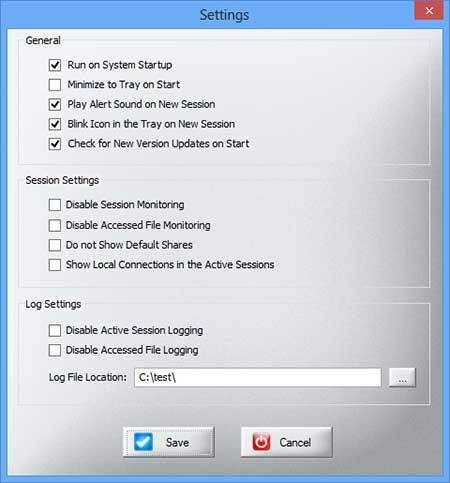
When you first start the program after installation, you are asked to select at least one drive, or a specific directory, that you want to scan for user access permissions. It is furthermore possible to exclude directories from being included in the scan, or activate the show members of groups option. Both the filter and email report options, while displayed in the interface, are reserved for users of the standard version of the application.
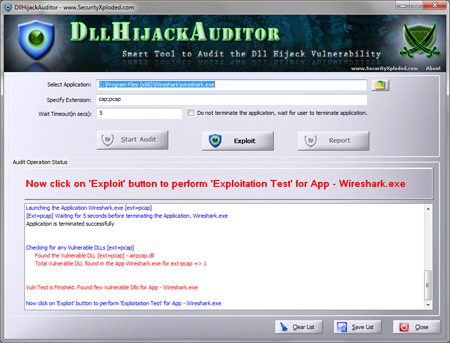
A click on the run report button in the interface scans the selected directories and drives for user permissions. This may take a while, depending on the amount of folders that need to be scanned, as well as the speed of the PC’s hard drive, and other activities.
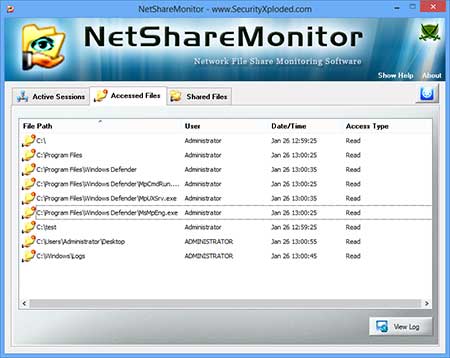
The results displays all user groups at the top, highlighting their rights on the drive or directory. NTFS Permissions Reporter furthermore displays scan errors in a log at the bottom of the screen. The tree view allows you to navigate through the folder structure, looking at access rights of specific folders.
When you select a folder, all user groups with access to the folder are displayed. You can click on a user group to see the permissions displayed on the screen in detail.
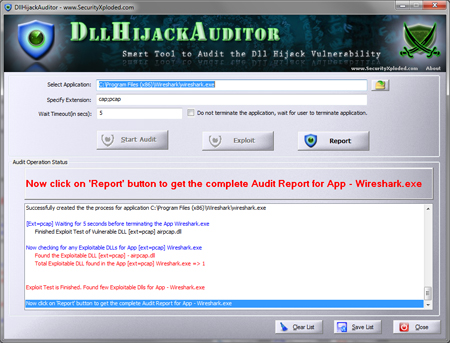
If you do not want to work with the tree view, you can switch to table view mode instead. This lists all scanned directories in a large table, along with user rights and related information.
You can click on a column header to sort the listing accordingly, for instance by permission, account, or display name.
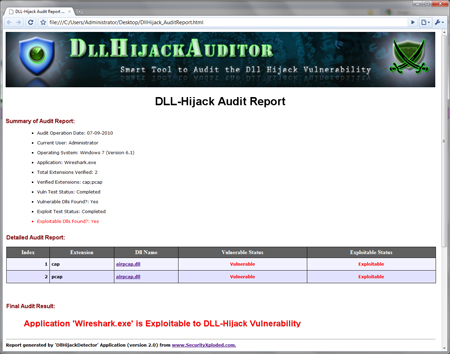
Reports can be exported to HTML files only in the free version of the program. The standard version of NTFS Permissions Reporter includes additional features, including the option to export to CSV, filters, and full command line support.
The software can only be installed on the system if the Microsoft .NET Framework 4.0 is installed on the system. Compatibility wise, it is compatible with all versions of Windows from Windows XP to the very latest.
Closing Words
If you want to make sure that user access rights on a Windows PC are configured the way they should be, either to check up on a PC’s security, or to make sure that users have sufficient rights to do what they are supposed to do, then NTFS Permissions Reporter is a tool that can aid you in that task.



.png)